Building the Course
The following RangeControl configurations were used
- ETHHACK.ps1 (Course Driver)
- ETHHACK.txt (Course Roster)
- ETHHACK.json (Course Config)
Initialize Course
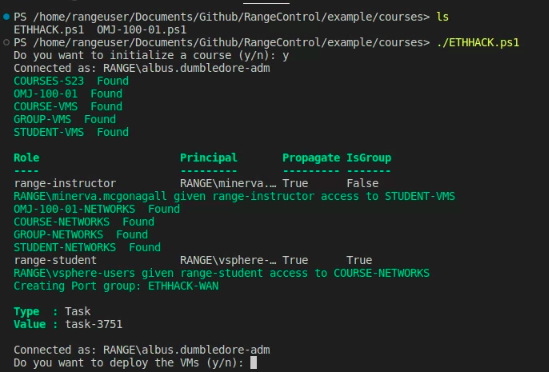
Initialize Networks
This is not required. Students will get an IP address on the COURSE-WAN and not have individual networks.
Deploy VMs
In this case, each student gets a Kali system and a windows system.
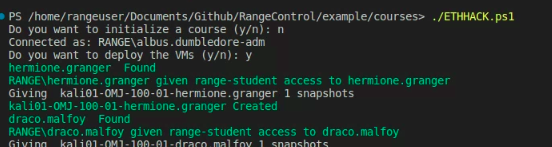
Networking
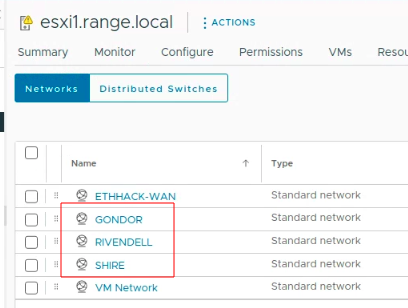
The Target Networks
These are additional and non standard course networks and so we will use raw PowerCLI to make this happen, the following documentation documentation shows how to do this. In the end you should have the following networks on esxi1
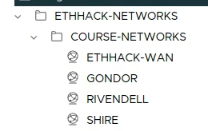
Manually drag these networks into the appropriate network inventory folder in vcenter.
The Course Gateway
The Course Gateway will differ slightly from the default presented as an example in the RangeControl documentation. It will include a DHCP server as well as a RIP relationship with a firewall that fronts the first of a series of target networks. Create a default version of the vyos course gateway as described here.
Add the following configuration to add a DHCP server and and a RIP advertisement.
set service dhcp-server global-parameters 'local-address 10.0.17.2;'
set service dhcp-server shared-network-name DHCPPOOL authoritative
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.17.0/24 default-router '10.0.17.2'
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.17.0/24 domain-name 'range.local'
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.17.0/24 lease '86400'
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.17.0/24 name-server '10.0.17.2'
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.17.0/24 range POOL1 start '10.0.17.20'
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.17.0/24 range POOL1 stop '10.0.17.199
set protocols rip interface eth1
set protocols rip network '10.0.17.0/24'
The Shire Firewall
The Shire network is directly accessible from systems on the ETHHACK-WAN and does not require imaginative pivoting and port forwarding and is suitable for an introductory Ethical Hacking class. The SHIRE firewall is also a vyos virtual machine that connects the ETHHACK-WAN and the SHIRE network segments. It has a stripped down configuration and No NAT source rules because we don't want target machines to reach out to the Internet. It will advertise the 10.0.5.0/24 network via RIP. SHIRE targets have a static DHCP entry so that they retrieve the appropriate IP address without having to configure a static IP address.
set interfaces ethernet eth0 address '10.0.17.3/24'
set interfaces ethernet eth1 address '10.0.5.2/24'
set protocols rip interface eth0
set protocols rip network '10.0.5.0/24'
set protocols static route 0.0.0.0/0 next-hop 10.0.17.2
set service dhcp-server shared-network-name DHCPPOOL authoritative
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.5.0/24 default-router '10.0.5.2'
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.5.0/24 domain-name 'shire.local'
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.5.0/24 lease '86400'
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.5.0/24 range POOL1 start '10.0.5.20'
set service dhcp-server shared-network-name DHCPPOOL subnet 10.0.5.0/24 range POOL1 stop '10.0.5.200'
set service ssh listen-address '10.0.17.3'
set system host-name 'fw-shire'
Static Mappings
As each target is provisioned and moved from ETHACK-WAN to one of the target networks, a static mapping should be made using the target's MAC address and desired IP address. This will be shown in the next section.
The Shire Name Server (ns.shire.org)
The Shire name server allows for students to use DNS enumeration techniques to find hosts on the SHIRE network. Here's an example configuration. The name server could be a Windows DNS Server, however a bind nameserver is lightweight. Here are some sample zones for bind9, listing the cupcake example target.
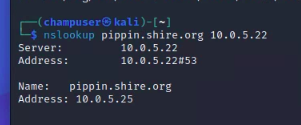
/etc/bind/named.conf.local
//
// Do any local configuration here
//
// Consider adding the 1918 zones here, if they are not used in your
// organization
//include "/etc/bind/zones.rfc1918";
zone "shire.org" {
type master;
file "/etc/bind/forward.shire.org.db";
};
zone "5.0.10.in-addr.arpa" {
type master;
file "/etc/bind/reverse.shire.org.db";
};
/etc/bind/forward.shire.org.db
$TTL 604800
@ IN SOA ns.shire.org. root.ns.shire.org. (
3 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
;@ IN NS localhost.
;@ IN A 127.0.0.1
;@ IN AAAA ::1
;Name Server Information
@ IN NS ns.shire.org.
;IP address of Name Server
ns IN A 10.0.5.22
;Mail Exchanger
shire.org. IN MX 10 mail.shire.org.
;A – Record HostName To Ip Address
cupcake IN A 10.0.5.23
/etc/bind/reverse.shire.org.db
;
; BIND reverse data file for local loopback interface
;
$TTL 604800
@ IN SOA shire.org. root.shire.org. (
1 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
;Name Server Information
@ IN NS ns.shire.org.
ns IN A 10.0.5.22
;Reverse lookup for Name Server
22 IN PTR ns.shire.org.
;PTR Record IP address to HostName
23 IN PTR cupcake.shire.org.